“There is no honor among thieves,” as the saying goes. As it turns out: that’s a good thing.
The latest example of this is the leak, last week, of internal documentation written by the Conti ransomware gang for the benefit of that group’s affiliates. An archive containing more than 100MB of training material (written in Russian), hacking tools and other confidential information was posted to a Russian hacking forum after a Conti affiliate complained he was paid only $1,500 for his part in a ransomware attack that netted the gang millions, Bleepingcomputer reported. The leak was first noted by a Twitter user using the handle @pancak3lullz, who shared links to the archive. The Russian language operating manual was subsequently translated into English and made available via a Github repository. (For the impatient, we have created a handy flowchart.)
It’s not personal. It’s strictly business.
If nothing else, the Conti playbook is a reminder (if any was needed) that internal security teams are no longer squaring off against disillusioned teenagers wielding Anonymous’ Low Orbit Ion Cannon DDoS tool at their public facing servers. Ransomware gangs are professional outfits with a wealth of knowledge and powerful tools at their disposal. And, as Michael Corleone famously observed in the Godfather: “It's not personal. It’s strictly business.”
For ransomware gangs, it’s strictly business. More specifically: it's strictly about getting the biggest ransom possible. That’s why step #1 in the playbook is about how to identify target companies. The documentation is pretty clear:
1.1 . Search for company income
The Conti gang provides a number of quick Google queries to do that but also recommends using more specialized business search engines like Dun & Bradstreet (dnb), Owler, Manta, Zoominfo, and Rocketrich to surface revenue information.

Conti provides their affiliates with powerful tools—first and foremost the ransomware—as well as supporting command and control (C2) infrastructure for managing the installed malware and exfiltrating stolen data. As the playbook shows, it also provides affiliates with detailed instructions for achieving dominion within enterprise environments. And, while Conti’s instructions to its affiliates are generic, the sad fact is that even generic guidance is good enough to work in most cases. Affiliates gain control over sophisticated enterprise environments with the information security equivalent of “painting by numbers.” That’s a bad look for the good guys.
But it also suggests that, as a defender, even modest improvements in defense, detection and incident response can be decisive. This is the “Fastest Camper in Bear Country” paradigm: steps you take are inconsequential in the larger struggle to rid the world of ransomware. But they can be very consequential in moving would-be attackers off of your network and onto another, less well protected environment.
Four Lessons from Conti University
Getting practical: defenders can glean a wealth of information from Conti’s playbook. Indeed, security teams everywhere should be auditing this free course at “Conti University.” Here are a four lessons we’ve picked out:
Lesson #1: Patch “Sensational” Flaws
Conti’s playbook provides a number of useful means to move laterally, escalate privileges and achieve dominion within compromised environments. Many of them pivot on exploiting critical, “10 out of 10” severity vulnerabilities. Among the flaws that Conti’s playbook specifically directs affiliates to leverage: EternalBlue (MS17-010), the Microsoft Zerologon vulnerability from 2020 and the more recent PrintNightmare remote code execution vulnerability (CVE-2021-34527) in Windows Print Spooler.
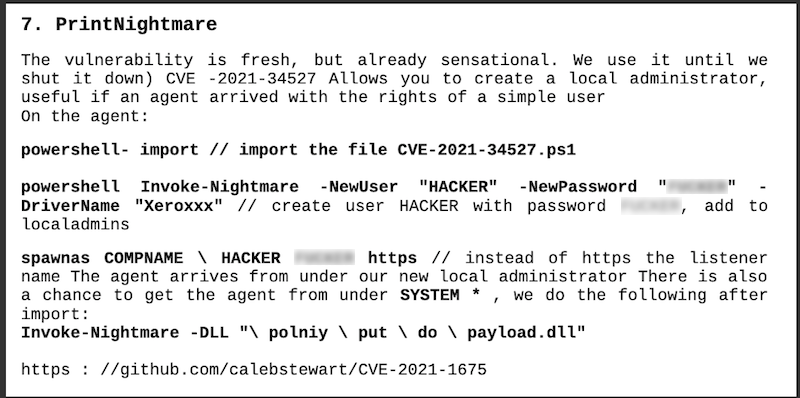
The takeaway from the Conti playbook: ransomware gangs aren’t messing around with 0days. Commodity vulnerabilities are good enough. So if you’re reading about a “10 out of 10” criticality flaw, it’s certain that the bad guys are going to exploit it as soon as possible. That should be an impetus for your organization to assess your exposure to that flaw and mitigate- or patch it as soon as humanly possible.
Lesson #2: Secure All The Endpoints
The other top-line takeaway is that organizations need to secure all their IT assets. True: ransomware attacks typically focus on the highest value endpoints, like application servers, file servers and critical databases. But the Conti playbook makes it clear that - at least in the lateral movement stage of an attack - the group is more agnostic in what endpoints it will target to expand its reach within an environment, obtain valuable credentials or elevate access. The playbook advocates use of tools like Router Scan to “brute-force” or exploit known software flaws in routers, cameras (and) NAS (Network Attached Storage)” devices.
Attacks on such devices can expose administrative passwords that can be “replayed” on higher value assets. In addition, NAS devices may be used to back up critical IT assets, so compromising them limits the ability of organizations to recover from attacks absent the ransomware gang’s decryption tool.
Lesson #3: Don’t get Roasted
The Conti playbook makes it clear that Kerberoasting is a favored method for obtaining administrator credentials from victim organizations. The best mitigation for Kerberoasting attacks, as we have noted, is to enforce robust password policies for service accounts. Organizations should mandate long, complicated passwords (25 or more characters) that are changed frequently.
The Conti playbook spills a good amount of ink instructing affiliates on how to look for weaknesses in an organization’s authentication regime: from the failure to “lock out” accounts after too many failed login attempts, to low thresholds for password complexity. In other words: your lax password practices—short passwords, infrequent password cycling, failure to prevent brute force attacks—sends a loud signal to Conti affiliates that your organization is one they should invest their time in.
On the detection side, organizations need to log and monitor activity related to user accounts. Technology such as QOMPLX’s Q:CYBER software monitors for telltale signs of Kerberoasting attacks, such as domain user accounts requesting large numbers of service tickets (Event 4769).
Lesson #4: Validate Authentication Traffic
Given the sheer number of Mimikatz variants and the ability of attackers to disguise their tooling or otherwise “live off the land,” organizations are better off looking for evidence of authentication attacks than trying to identify Mimikatz out of the box.
This is an area where we specialize. Q:CYBER uses a combination of rules, statistics, and machine learning to tease out evidence of nascent attacks from network and endpoint telemetry and other security monitoring devices. For example, we employ a Sysmon-based heuristic to detect a pattern of LSASS access that is typical of Mimikatz.
Beyond that, we verify that each Kerberos authentication event is traceable back to legitimate user interactions with the issuing domain controller, and that Kerberos tickets were correctly generated and issued. By making Kerberos “stateful” in this way, defenders can spot Kerberos ticket forgeries like Golden and Silver Ticket attacks as they happen.
Organizations that are serious about stopping groups like Conti need to be able to similarly police the authentication activity within their environment. The Conti playbook makes clear that subverting authentication is Job One for affiliates. Any security technology that presumes authenticated user activity is legitimate activity is of little use in identifying or stopping groups like Conti.
Good hunting!





