New research from Cybereason exposes how fast cybercriminals can take over a network, after the initial infection of a corporate user account, by leveraging well known malware IcedID and the common identity attack tool, Rubeus.
While IceID as a malware strain is not new or novel in itself, this latest campaign demonstrates how IcedID is being leveraged in new and inventive ways. Moving beyond simple spam phishing campaigns, to now proliferating as an infected Zoom software update. What is further seen as part of this research is the advanced focus on establishment of an identity based stronghold as a core feature of its initial compromise. This campaign truly highlights how non-zero day malware continues to run rampant in enterprises despite the latest and greatest AI capabilities from next-gen EDR players.
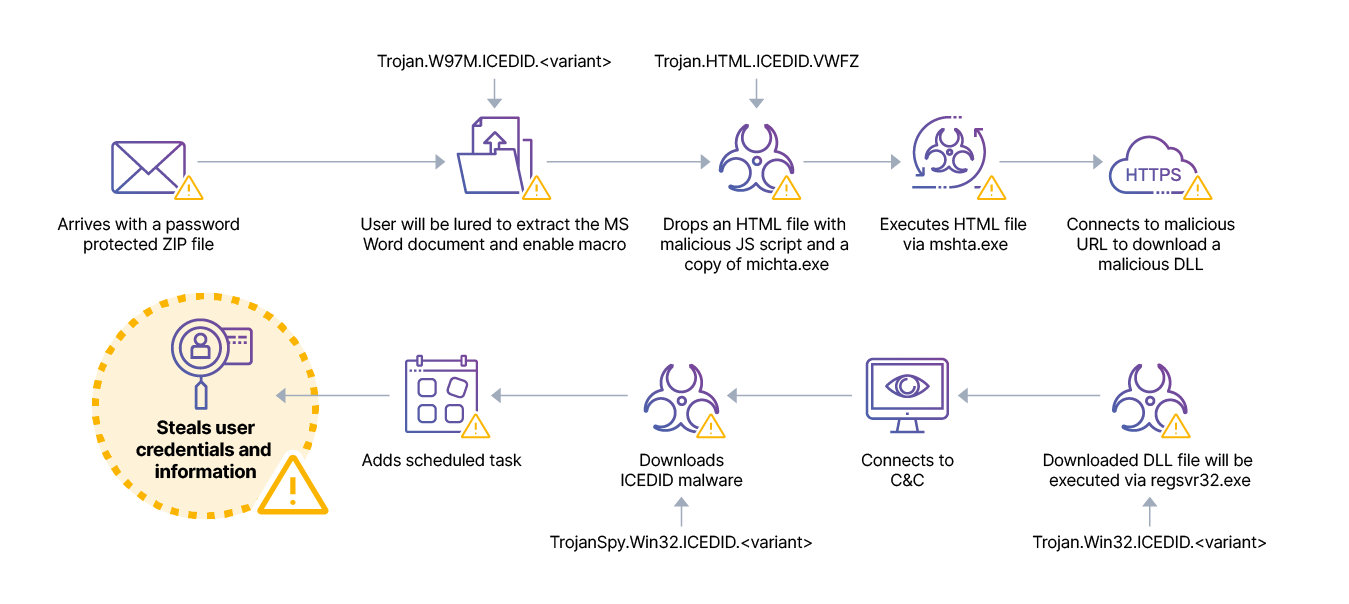
Attack chain
The attack chain observed is broken down into multiple stages, each taking advantage of the latest beach heads as part of their next stage of infection. In multiple stages we see lateral movement and privilege escalation tactics as key components of IcedID's strategy to quickly gain domain dominance.
IcedID makes its initial infection via an infected archive containing an ISO and deceptive LNK file. Once IcedID has completed the infection process, Cobalt Strike code is used to load the common hacker tool Rubeus, which is well known for its capabilities for abusing identity within Windows environments.
Research from Cybereason as detailed below shows how the attacks work:
The Cobalt Strike code loads Rubeus, a tool designed for Kerberos interaction and abuse, which also collects more network data from the system. Attackers obtain the credentials of a service account via Kerberoasting, a known technique based on abusing valid Kerberos tickets, 15 minutes after the initial infection.
57 minutes after the infection, the lateral movement operation starts. The attacker uses the legitimate command line tool ping.exe from the system to check if the host is alive, then executes the same Cobalt Strike payload on the remote workstation via wmic.exe. That process is repeated several times, each time bouncing on a different endpoint or server. Large portions of the network infrastructure are scanned.
A DCSync attack is performed 19 hours after the initial compromise. This technique allows an attacker to impersonate a domain controller to obtain password hashes from other domain controllers, enabling the attacker to increase their foothold on every domain of the targeted company.
Shortly before the exfiltration starts and 46 hours after the initial infection, the attackers deploy the legitimate Atera remote administration tool on several different machines. The implementation of that tool on several computers allows the attackers to come back to the system even if the IcedID malware is discovered and computers are cleaned from it.
At this stage IcedID has all of the privileges and permissions required to use the common open-source tool, Rclone, to exfiltrate any data and then encrypt the data to achieve the desired financial objective.This is often completed in a mere 50 hours.
How QOMPLX detects IcedID
In multi-stage attacks like IcedId there are many areas where a defender can step in and halt the attack progression. Below are the areas where QOMPLX can step in and support an organization's overall security strategy.
While having an AV or EDR solution in place is always a good part of a “Defense in Depth” security strategy, there are times when malware finds a way to bypass or trick those tools. As backup to those tools QOMPLX has detection rules and content in place to gain visibility into LSASS manipulation which is commonly used by various attacker tools looking to target both identity and authentication attack vectors with tools such as Mimikatz or as in IcedID’s case Rubeus.
The attacker started using native Windows utilities and tools like PING and WMIC to enumerate the network. QOMPLX has the “Windows Built-In Utility Detection'' that can monitor and detect this behavior when multiple enumeration commands are executed within a certain time window, grouped by when they come from the same host, allowing for easy fine tuning and customization.
During the third phase of the IcedID attack chain we saw that Kerberoasting and DCSync attacks were done in order to gain higher rights and privileges. QOMPLX has native detections for both these attacks. In addition to live attack detection QOMPLX also supports a prevention first capabilities, by being able to identify accounts that would be susceptible to attacks such as Kerberoasting or similar attacks such as AS-REP Roasting.
In summary
Across the entire cybersecurity landscape defenders are consistently seeing expanded prevalence of identity related components in both re-tooled legacy malware and new zero-day strains as well. This has caught AV/EDR vendors in the proverbial cat-mouse game, leading to a highly prioritized focus on identity based attack prevention and detection tooling that is being classified by industry analysts such as Gartner via their research on ITDR (Identity Threat Detection and Response).


