When the healthcare provider Medibank released their 2023 half-year results in late February, the 2022 breach was front and center in their public disclosure and the CEO’s video announcement. Let’s look at the findings to see what lessons we can learn from the breach.
Why is the NIST CSF Supply Chain Risk Management Requirement so important?
According to reports, the Medibank breach was caused, initially, by a misconfiguration in a third-party vendor's network firewall. This incident highlights the need for CISOs to pay close attention to the security posture of third-party vendors and ensure they have adequate security controls in place.
Defenders need to understand and have full visibility into their organization’s security posture from both an outside perspective as well as from their internal posture. This will help to prevent criminals from breaching their network perimeter and reduce the dwell time of attackers. These insights can be gained from Attack Surface Management which provides the size and depth of vulnerabilities in your external threat landscape as well as identifies third party risks through supply chain risk monitoring or EASM (External Attack Surface Monitoring).
How attacks are taking advantage of data/services relationships
In the Medibank breach, the attackers were able to “land and expand” from a single stolen password to the exfiltration of patient data. This points squarely to a weakness in the identity infrastructure, proving that there is a need to improve their identity security posture. According to Gartner®, the preventive controls assist identity security posture management in order to avoid:1
- “Misconfiguration, by ensuring IAM controls are properly configured, that the IAM configuration is continuously monitored for suspicious changes, and that appropriate steps are taken to investigate and, if necessary, resolve issues”
- “Vulnerabilities, by addressing commonly exploited vulnerabilities in the identity infrastructure via patching or compensating controls.”
- “Exposure, by reducing the attack surface by removing unnecessary or excessive privileges, for example.”
CISOs should prioritize these activities to ensure that their security controls are effective in mitigating cyber risks, especially those posed by Identity Threats.
Where does Identity Security come in?
The Medibank breach was reportedly undetected for several months, allowing the attacker to steal sensitive information without being detected. CISOs must prioritize identity threat detection & response to identify and respond to cyber threats that target the very foundation of the modern enterprise, the digital identity.
In October 2022, Gartner published a report to help organizations prepare the much needed capabilities for Identity Threat Detection and Response (ITDR).2 Their recommendations were clear and concise:
Security and risk management leaders focused on identity and access management should:
- “Prepare for ITDR with hygiene measures by inventorying their existing prevention controls and auditing their IAM infrastructure for misconfigurations, vulnerabilities and exposures.”
- “Enhance detection controls by choosing a focal point for identity alert correlation and detection logic that prioritizes identity tactics, techniques and procedures (TTPs) above other detection mechanisms.”
- “Master the response phase by building or updating playbooks and automation to include IAM enforcement within the steps taken to eradicate, recover from, report and remediate identity threats. Integrate IAM incidents into response and threat-hunting processes using existing security controls in the security operations center (SOC).”
- “Fill gaps in ITDR by assessing the full range of attack vectors and telemetry covered. Plan to use a mosaic of tools that complement each other, and may overlap, to meet the requirements for a comprehensive ITDR initiative.”
The focus of ITDR is to work as second and third layers of defense (see Figure below), after the foundational preventive mechanisms identified above are in place.
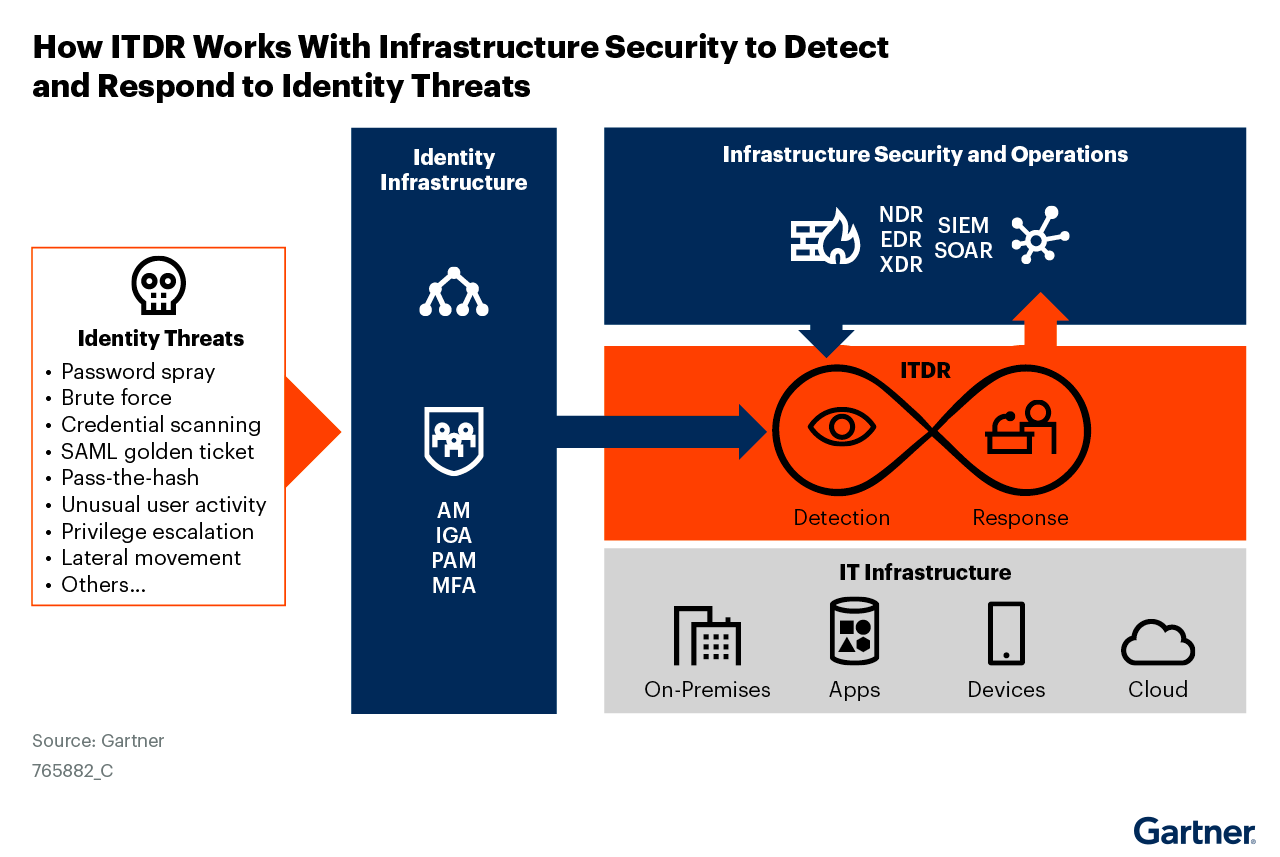
Cyber incidents are inevitable, and having an incident response plan in place can help organizations respond quickly and effectively to minimize the impact of a breach. CISOs should ensure that their incident response plans are regularly tested and updated to address emerging cyber threats, especially those targeting digital identities which are the very foundation of the Zero Trust architecture.
How QOMPLX can help
As we learn from the Medibank breach, CISOs need to focus on their organization’s attack surface, as well as their third-party vendors’, regular security assessments and penetration testing, and identity threat detection & response . CISOs can use these insights to strengthen their organizations' cybersecurity posture and reduce the risk of a cyber breach with a 3 prong approach:
To provide a prevention first capability, QOMPLX’s Q:SCAN is designed to perform Attack Surface Monitoring and Third Party Risk Management with the kind of security signals that the CISOs can use to understand their organization’s security posture, as well as their supply chain vendors.
Looking at inside the enterprise IT environment, the QOMPLX Privilege Assurance solution performs risk assessment on your Active Directory and Azure Active Directory on a continuous basis and helps identify any exposure to common identity exploitation paths that an attacker may take advantage of if they are inside your environment.
Lastly, for live identity attack detection, QOMPLX Identity Assurance is capable of detecting common identity class attacks such as Password spray, Brute force, Kerberos/SAML Golden tickets, Pass-the-hash, DCSync, DCShadow, and many more attacks that target the identity in the enterprise and in the cloud. This approach provides full feature identity security for organizations.
1 Gartner, Enhance Your Cyberattack Preparedness With Identity Threat Detection and Response, Henrique Teixeira, Peter Firstbrook, Ant Allan, Rebecca Archambault, Published 20 October 2022
2 Ibid., p.3
Disclaimer
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.





