This is the latest in a series of posts we’re calling “QOMPLX Knowledge.” These posts are intended to provide basic information and insights about the attack activity and trends that are driving malicious campaigns and that QOMPLX researchers encounter in our forensic work with customers.
Cyber adversaries who compromise an IT environment are keen to avoid detection. One way they do that is by “living off the land.” That is: they use existing administrative tools, rather than external programs or malware, to carry out their objectives. The other method is to encrypt or encode commands and other communications to avoid tripping alerts tied to specific commands or actions. Organizations that want to spot and stop sophisticated cyber actors need to pay attention to the use of both “dual use” applications and monitor for efforts to disguise network activity using encryption or encoding.
Microsoft’s PowerShell is one of the most commonly used applications for adversaries seeking to “live off the land.” In this post, we’re taking a look at how QOMPLX’s technology helps customers to spot one technique that attackers use to disguise their use of PowerShell by running it in the background of another application.
Key Points
- Monitoring for the use of PowerShell is an important means of spotting efforts by malicious applications or actors to conduct surveillance or execute malicious code without being noticed.
- Logging PowerShell activity is critical to monitoring for malicious activities.
- Windows Event ID 4688 (a new process has been created) is a critical event for monitoring processes created with the command line.
- PowerShell sessions that are launched by other, unrelated applications are suspicious and may indicate efforts to conceal use of PowerShell to run malicious commands or reconnaissance activity.
- QOMPLX’s Identity Assurance product monitors for Windows Event ID 4688 in which a non-interactive PowerShell session is executed by another application in the background.
How Background Execution of PowerShell Works
PowerShell is a cross-platform task automation solution for Windows environments. It has been shipped by default with Windows systems beginning with Windows 7 SP1 and Windows Server 2008 R2 SP. PowerShell includes a command-line shell, a scripting language, and a configuration management framework and runs on Windows, Linux, and macOS.
Because of its power and ubiquity, PowerShell is a popular “dual use” technology: assisting network IT administrators but also popular among “red teams” and malicious actors who want to expand their reach within networks without having to import malicious software that might be detected by endpoint or network monitoring software. PowerShell is a common tool for “living off the land” within compromised environments and has been incorporated into a number of post-exploitation kits with names like PowerSploit, PowerShellEmpire, BloodHound, EmpireProject, Powershell-C2 and more.
Any new processes launched in Windows trigger Windows using Event ID 4688 (a new process has been created). Assuming that monitoring of this event is taking place, organizations can monitor for the use of PowerShell and verify how the application was invoked. Typically, the “Creator Process” would be explorer.exe.
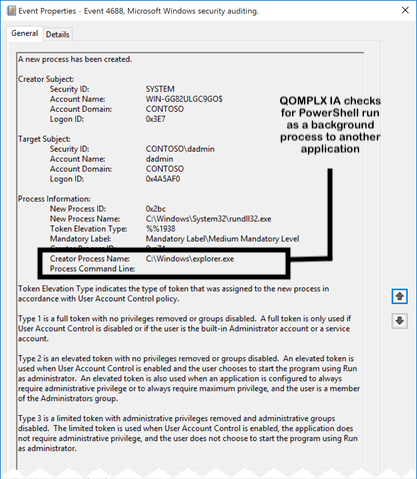
To avoid detection, however, attackers often conceal the use of PowerShell by invoking it from within other applications, such as Microsoft Word, Excel or other applications. While there are legitimate reasons for PowerShell to be invoked in the background, such as administrative scripts or other approved automation, launching PowerShell from within an unrelated application (like Word) is a red flag that malicious actors are attempting to conceal their use of PowerShell within an environment.
QOMPLX Detection
QOMPLX Identity Assurance can detect instances in which PowerShell is invoked in the background. This detection monitors Windows Event ID 4688 for processes with non-interactive PowerShell sessions that were executed by another application in the background. PowerShell instances that have a parent process other than explorer.exe are considered “background use” and flagged by QOMPLX IA.
Additional Reading
QOMPLX Knowledge: Detecting Account Name Enumeration
QOMPLX Knowledge: Detecting New Members Added To Sensitive Groups
QOMPLX Knowledge: Detecting Password Spraying Attacks
Q:CYBER Ingesting Windows Event Logs
Q:CYBER Using Windowed Rules for Advanced Detection
QOMPLX Knowledge: Golden Ticket Attacks Explained
QOMPLX Knowledge: Silver Ticket Attacks Explained
QOMPLX Knowledge: Responding to Golden Ticket Attacks
QOMPLX Knowledge: DCSync Attacks Explained
QOMPLX Knowledge: DCShadow Attacks Explained
QOMPLX Knowledge: Pass-the-Ticket Attacks Explained
QOMPLX Knowledge: Kerberoasting Attacks Explained
Understanding Zones and Zone Transfer
Security Monitoring Recommendations for Windows Event 4688
Learn More
Use the following form to request more information about QOMPLX detection of sophisticated attacks and other threats.





